Solutions | TruContext Capabilities
TruContext™ Capabilities
Visualize Real Time Events
Every event happens at a point or duration in time. Successful investigations need to understand how those events unfold, and how they’re linked. With TruTime, our interactive timeline feature, you can quickly see when something happened, allowing further investigation into what changed at that specific point in time.
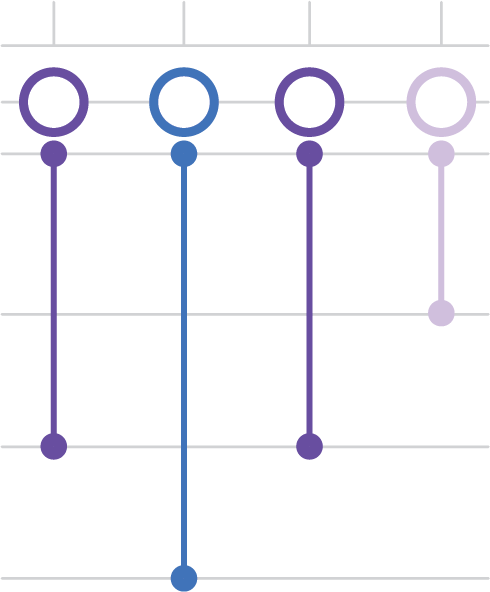

The Analysis Dashboard
With TruContext™, you can point, click, and submit automated queries. Code Editor can be used if you know cypher query language and want a different structure.
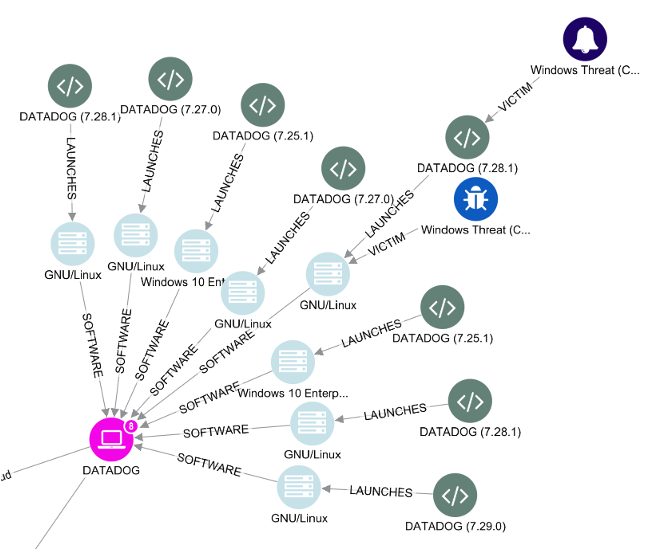
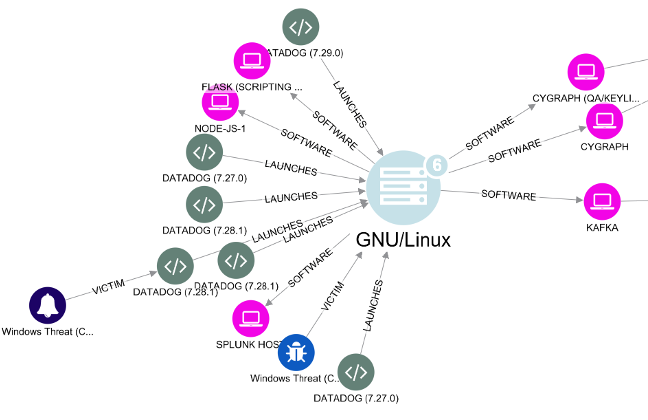
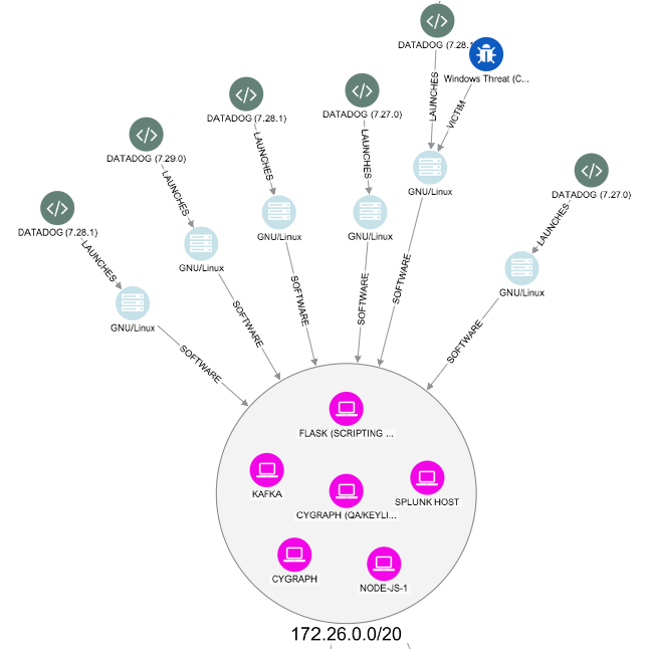
Threat Hunting and Threat Detection
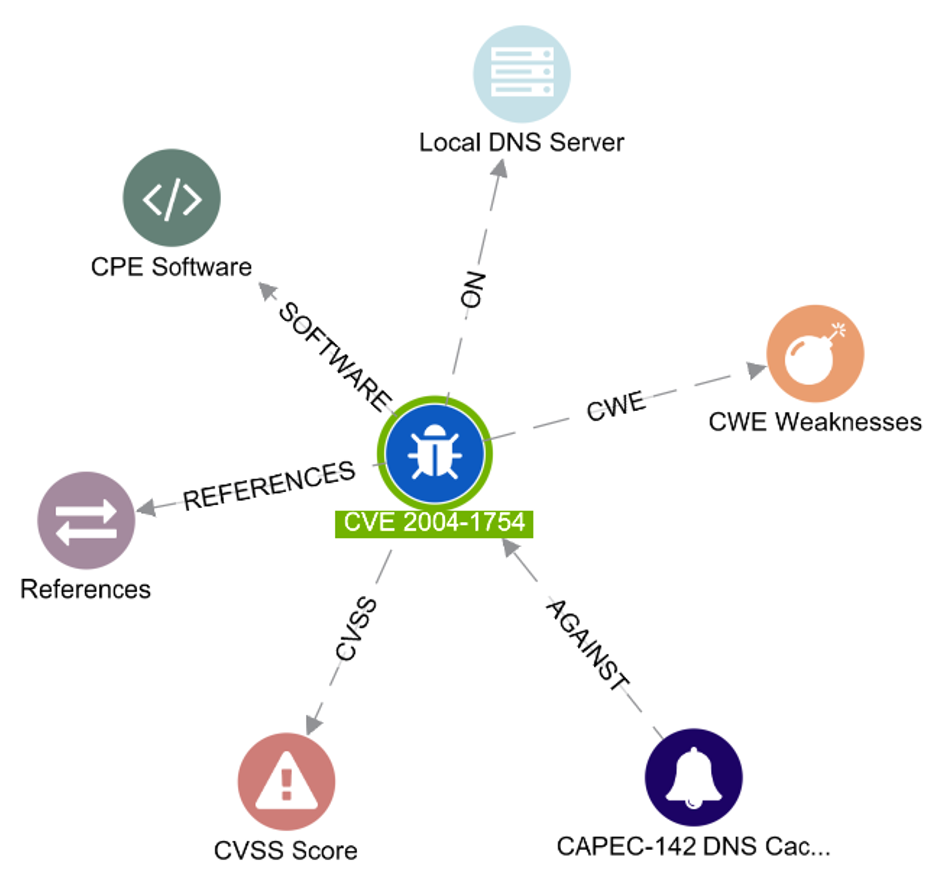
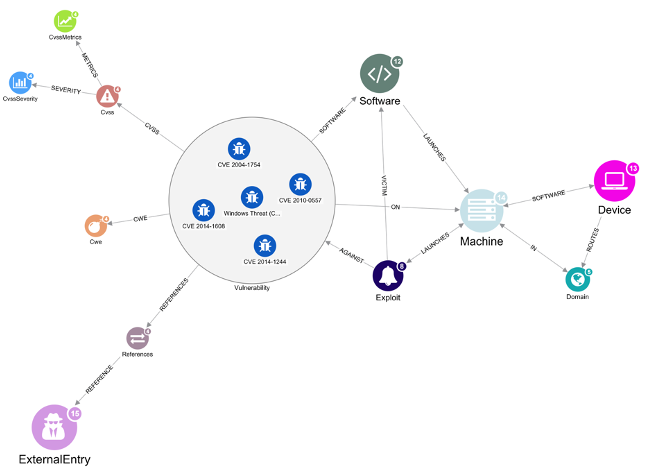
VULNERABILITIES
- Dive deep into vulnerabilities and display everything that is connected to identify it as a potential risk
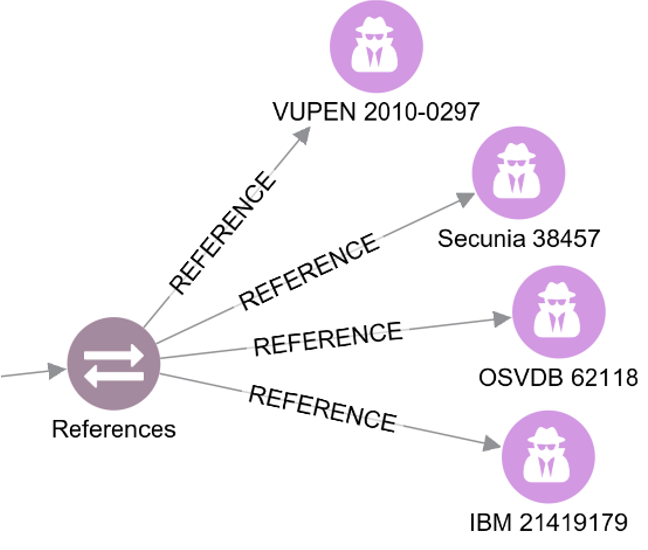
- The table view displays the properties of the identified CVE vulnerability as identified by the MITRE reference database which will enable you to take immediate action on that CVE
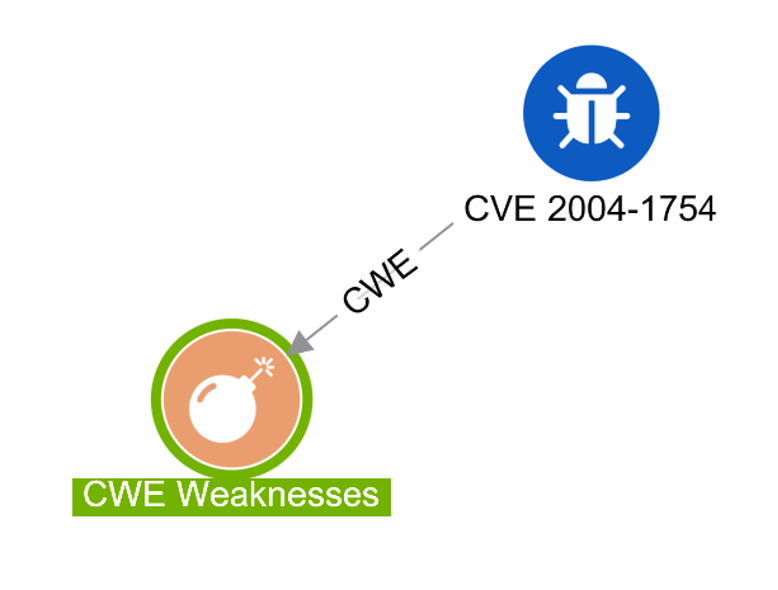
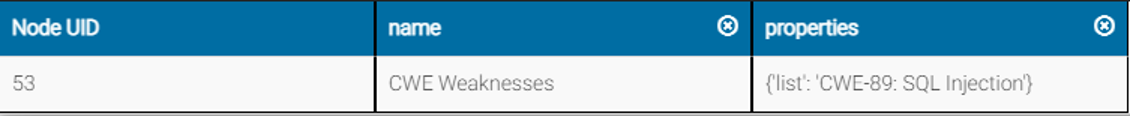
COMMON WEAKNESS ENUMERATION (CWE™)
- The main goal of CWE is to stop vulnerabilities at the source by educating software and hardware architects, designers, programmers, and acquirers on how to eliminate the most common mistakes before products are delivered. Ultimately, use of CWE helps prevent the kinds of security vulnerabilities that have plagued the software and hardware industries and put enterprises at risk.
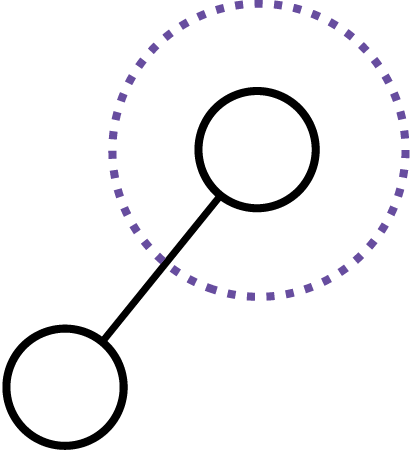
Incident Response
FILTERING
From the selected view we can filter based on the following:

FAQs
There are many definitions of vulnerability. Here is a list of definitions from various cybersecurity authorities.
- National Institute of Standards and Technology (NIST): Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
- ISO 27005: A weakness of an asset or group of assets that can be exploited by one or more cyber threats where an asset is anything that has value to the organization, its business operations and their continuity, including information resources that support the organization’s mission.
- IETF RFC 4949: A flaw or weakness in a system’s design, implementation, or operation and management that could be exploited to violate the system’s security policy.
- ENISA: The existence of a weakness, design, or implementation error that can lead to an unexpected, undesirable event compromising the security of the computer system, network, application, or protocol involved.
- The Open Group: The probability that threat capability exceeds the ability to resist the threat.
- Factor Analysis of Information Risk: The probability that an asset will be unable to resist the actions of a threat agent.
- ISACA: A weakness in design, implementation, operation or internal control.
- A zero-day exploit (or zero-day) exploits a zero-day vulnerability. A zero-day (or 0-day) vulnerability is a vulnerability that is unknown to, or unaddressed by, those who want to patch the vulnerability.
- Until the vulnerability is patched, attackers can exploit it to adversely affect a computer program, data warehouse, computer or network.
- “Day Zero” is the day when the interested party learns of the vulnerability, leading to a patch or workaround to avoid exploitation.
- The key thing to understand is the fewer days since Day Zero, the higher likelihood that no patch or mitigation has been developed and the higher the risk of a successful attack.
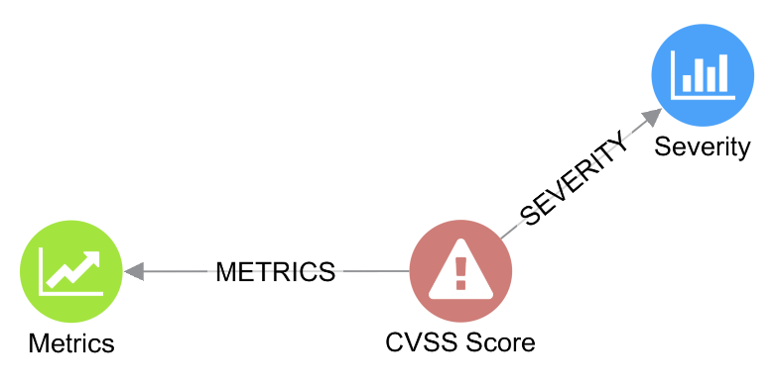
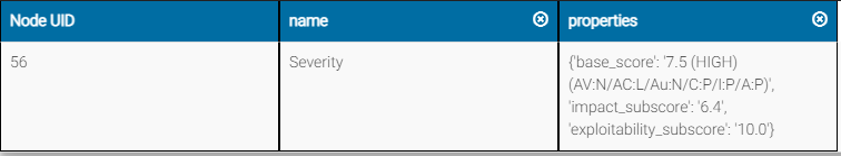
- The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
- CVSS is a published standard used by organizations worldwide, and the SIG’s mission is to continue to improve it.
- Common Weakness Enumeration (CWE™) is a community-developed list of common software and hardware weakness types that have security ramifications. “Weaknesses” are flaws, faults, bugs, or other errors in software or hardware implementation, code, design, or architecture that if left unaddressed could result in systems, networks, or hardware being vulnerable to attack. The CWE List and associated classification taxonomy serve as a language that can be used to identify and describe these weaknesses in terms of CWEs.