Solutions | MITRE ATT&CK
MITRE ATT&CK
What is MITRE ATT&CK?
The MITRE ATT&CK Framework is a curated knowledge base that tracks cyber adversary tactics and techniques used by threat actors across the entire attack lifecycle. The framework is meant to be more than a collection of data: it is intended to be used as a tool to strengthen an organization’s security posture.
For instance, because MITRE ATT&CK takes the perspective of the adversary, security operations teams can more easily deduce an adversary’s motivation for individual actions and understand how those actions relate to specific classes of defenses.
ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, includes detailed descriptions of advanced persistent threat (APT) groups’ observed tactics (the technical objectives they’re trying to achieve), techniques (the methods they use), and procedures (specific implementations of techniques), commonly called TTPs.
Understanding the ATT&CK Framework
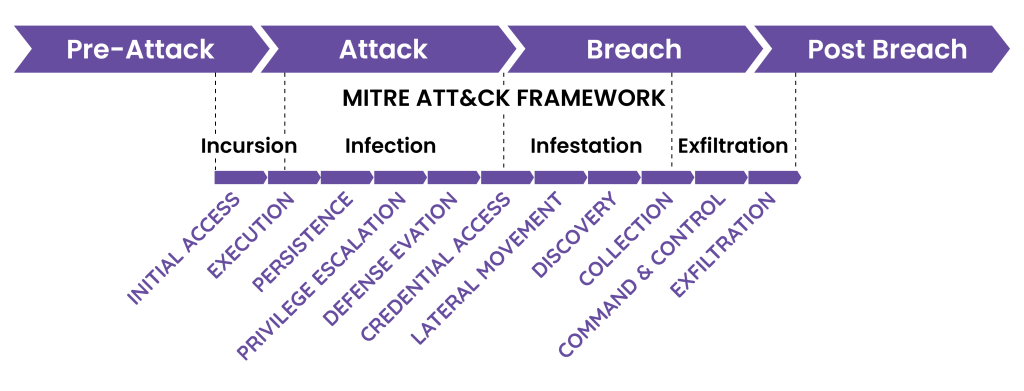
Attackers operate differently depending on their attack target. For example, they use different TTPs to compromise enterprise systems than they would to attack mobile devices or industrial control systems. MITRE provides three separate “matrices” to address these distinct environments. Together, these three matrices make up what MITRE collectively refers to as the ATT&CK framework.
The Enterprise matrix addresses platforms such as Windows, macOS, Linux, and others as well as something called “PRE,” which simply indicates actions taken pre-attack or in preparation for an attack. The Mobile matrix addresses both Android and iOS, and the ICS matrix addresses industrial control systems. Although the three matrices share some common tactics (Initial Access and Persistence, for example), the specific techniques for each tactic can vary by environment.
The History of MITRE ATT&CK
MITRE is a nonprofit organization created to provide engineering and technical guidance to the federal government. The organization introduced ATT&CK in 2013 as a way to describe and categorize adversarial behaviors based on real-world observations. MITRE ATT&CK was released to the public for free in 2015, and today helps security teams in all sectors secure their organizations against known and emerging threats.
ATT&CK is a structured list of known attacker behaviors that have been compiled into tactics and techniques and expressed in a handful of matrices as well as via STIX/TAXII. Since this list is a fairly comprehensive representation of behaviors attackers employ when compromising networks, it is useful for a variety of offensive and defensive measurements, representations, and other mechanisms.
ATT&CK Matrix for Enterprise: Tactics and Techniques
It’s important to understand how MITRE ATT&CK defines tactics and techniques. When looking at ATT&CK in the form of a matrix, the column titles across the top are tactics and are essentially categories of techniques. Tactics are the what attackers are trying to achieve whereas the individual techniques are the how they accomplish those steps or goals.
- Tactics: Describes the immediate technical objectives (the “what”) attackers are trying to achieve, such as gaining Initial Access, maintaining Persistence, or establishing Command and Control.
- Techniques: Describes the “how”—the methods attackers use to achieve a tactic. All tactics in each matrix have multiple techniques; the Enterprise matrix breaks some techniques down further into sub-techniques.
What Can be Accomplished with MITRE ATT&CK?
MITRE ATT&CK is a highly detailed repository of information about real-world adversary groups and their known behavior. Unlike other models written from a defender’s perspective, ATT&CK takes an attacker’s point of view to help organizations understand how adversaries successfully execute attacks. This makes it a uniquely valuable tool for helping organizations gain insight into attacker behavior so they can improve their own defenses.
MITRE ATT&CK Use Cases
ATT&CK is a free tool that organizations of all sizes and industries have widely adopted. The wealth of information it contains can help organizations determine whether they’re collecting the right data to effectively detect and prevent attacks.
ATT&CK is valuable in a variety of everyday settings. Any defensive activities that reference attackers and their behaviors can benefit from using ATT&CK. Common uses include:
- Mapping defensive controls
- Threat hunting
- Detections and Investigations
- Referencing actors
- Tool integrations
- Red Team/Penetration Test Activities

The MITRE ATT&CK Framework and Visium Analytics
Visium Analytics has recently launched its integration with the MITRE ATT&CK Framework, which now, along with TruContext, delivers insight into exactly where to focus efforts during any phase and state of a cyber-attack. As depicted below, the phases could be anywhere from catching compromises in real-time at the pre-attack point to high velocity root cause analysis at the breach point. Combined with ATT&CK, Visium Analytics is uniquely positioned to deliver immediate and human understandable focus of an attack radius so that time limited resources, cyber professionals, can zero in on highest impact targets and priorities.
ATT&CK as a guiding framework