Solutions | Use Cases | Critical Infrastructure (IT/OT/IOT)
USE CASES
Critical Infrastructure (IT/OT/IOT)
Build the Secure Infrastructure you Need to Understand Connections
Detect Security Violations
0
%
Faster
Graph
0
%
of your IT/OT/IOT network and instantly see if your devices are communicating to the internet
Issues and Challenges
Building a secure infrastructure is all about understanding connections. From cellular networks, transportation routes, gas pipelines, to corporate IT systems; they’re all complex connected systems. A single point of failure within the network can have devastating impacts.
With every connected device or machine generating a digital footprint, it’s easy to produce infrastructure data on a massive scale. The challenge we face is connecting the dots. That’s where network mapping software and data visualization plays a crucial role.

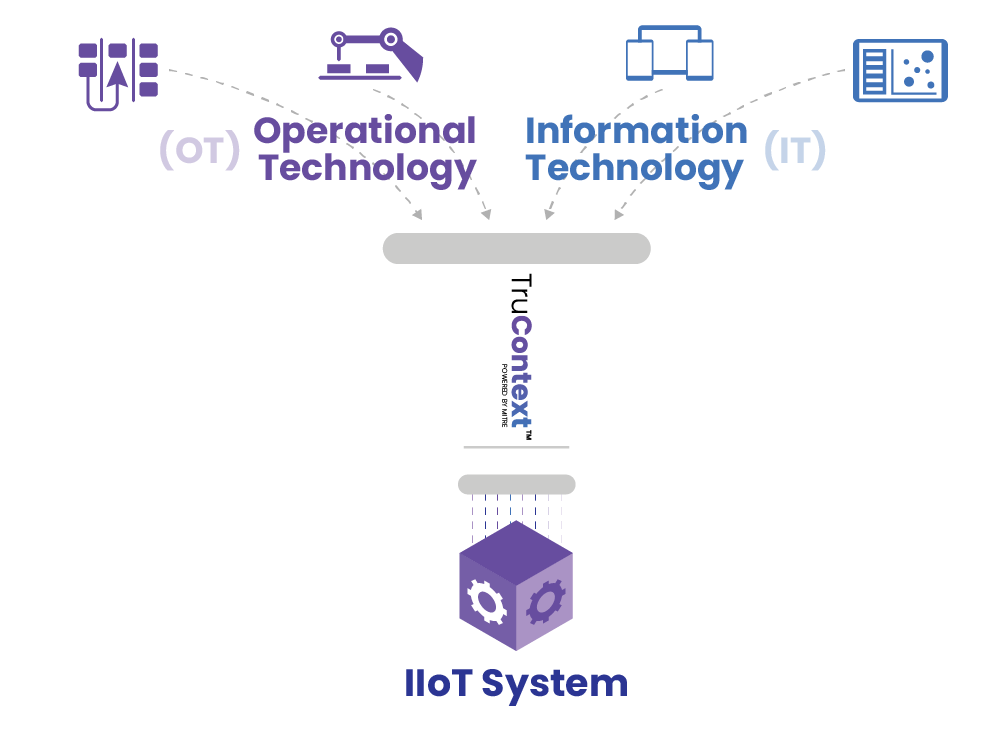
The TruContext™ Solution
Every day, billions of events can take place in a single network. To make sense of all the disparate pieces of information, analysts need to see what’s happening from the right perspective. TruContext allows users to see their data from a vantage point that explains the connections in their critical infrastructure. Network mapping software makes it easier and faster to uncover vulnerabilities and bottlenecks in critical infrastructure networks. These scale from a single connection to tens of thousands, revealing network patterns and specific device behavior.

Value to Customer
The Purdue Model has provided a hierarchical structure for industrial communications to keep computing and networks deterministic. But in the age of IoT, data flow is no longer hierarchical.
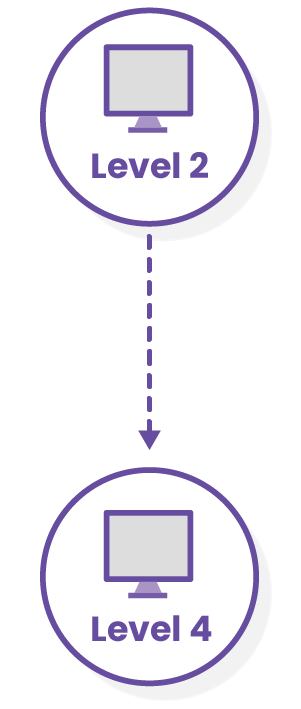
TruContext has been able to capture relevant sensor data from older iconic systems so you can quickly see the device and where it communicates in the Purdue Model. For example, you can quickly identify if a device on Level two is talking to or connected to a device on Level 4 which would be a violation.
TruContext’s underlying Cygraph technology is deployed within the Army Cyber command and is able to prioritize exposed vulnerabilities in mission-critical assets. In the face of attacks, it correlates intrusion alerts to known vulnerability paths and suggests courses of action. For post-attack forensics, it shows vulnerable paths that warrant deeper inspection for faster event analysis.