TruContext clients can effectively see all their data while practically eliminating the data conditioning workload. This is done natively by TruContext with the results being fully functional and usable cyber graphs providing a full context of the data.
Our architecture has the following component layers which bring value to the user:
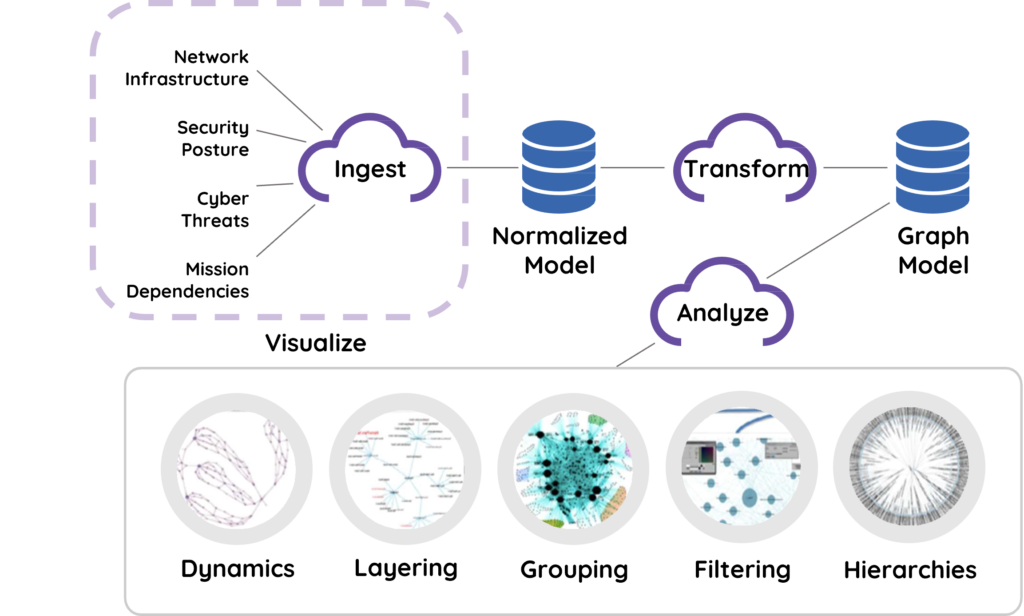 1) Your Cyber Tools and other Source Data is ingested into TruContext
1) Your Cyber Tools and other Source Data is ingested into TruContext
- TruContext ingests data from anywhere at anytime.
- TruContext can be integrated into any security management system. No more tool sprawl!
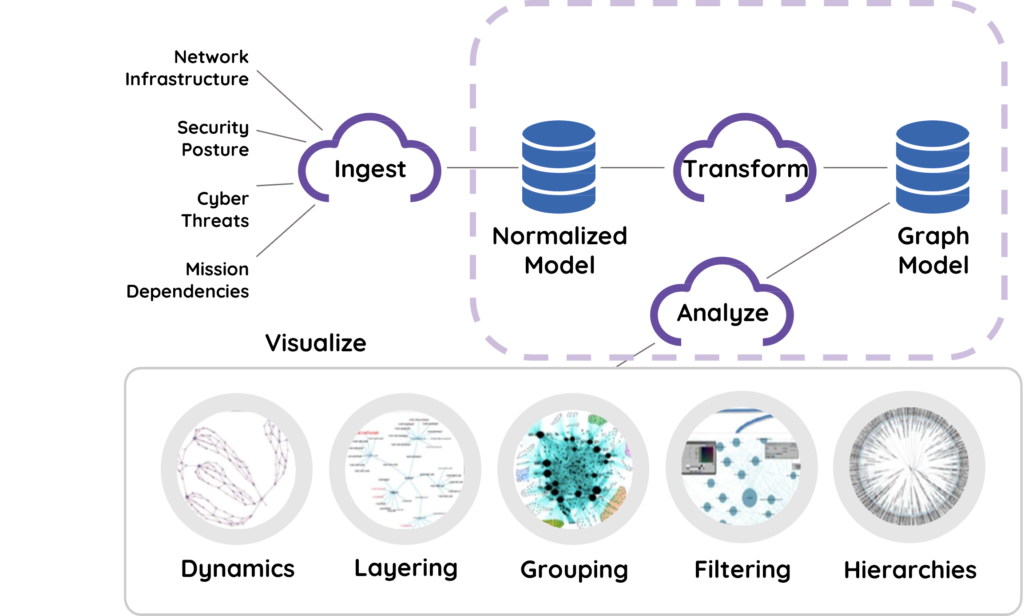 2) Your High-Priority Assets are Identified, Labeled, and Categorized
2) Your High-Priority Assets are Identified, Labeled, and Categorized
- Multiple, disparate data is organized into an overall picture in real-time!
- This allows prioritization for remediation to your most valuable assets!
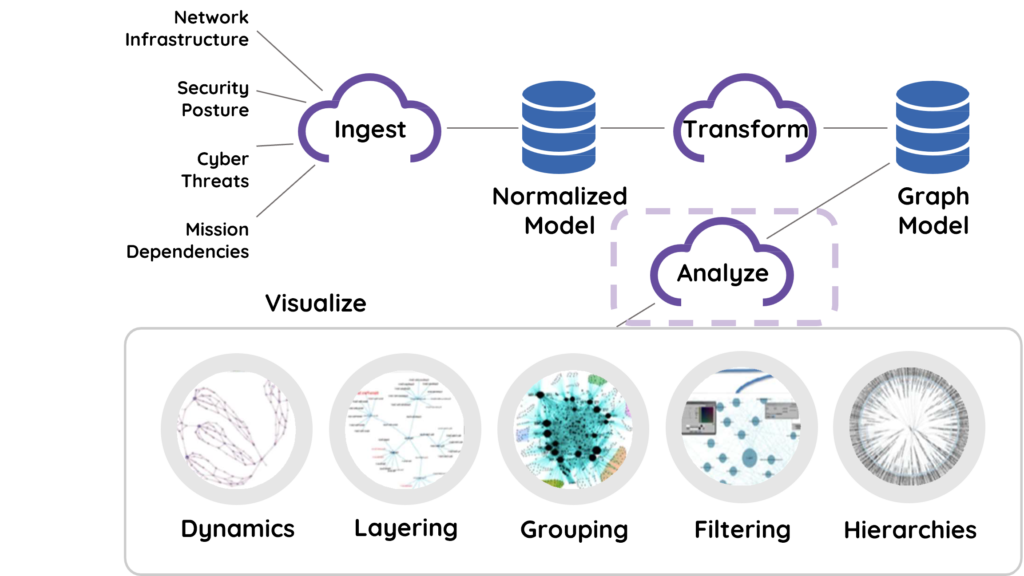
3) Patented Analytics and Correlations of your Enterprise Assets
- Turn information into knowledge!
- Analytics provide deep and understandable insights into aggregated data sets.
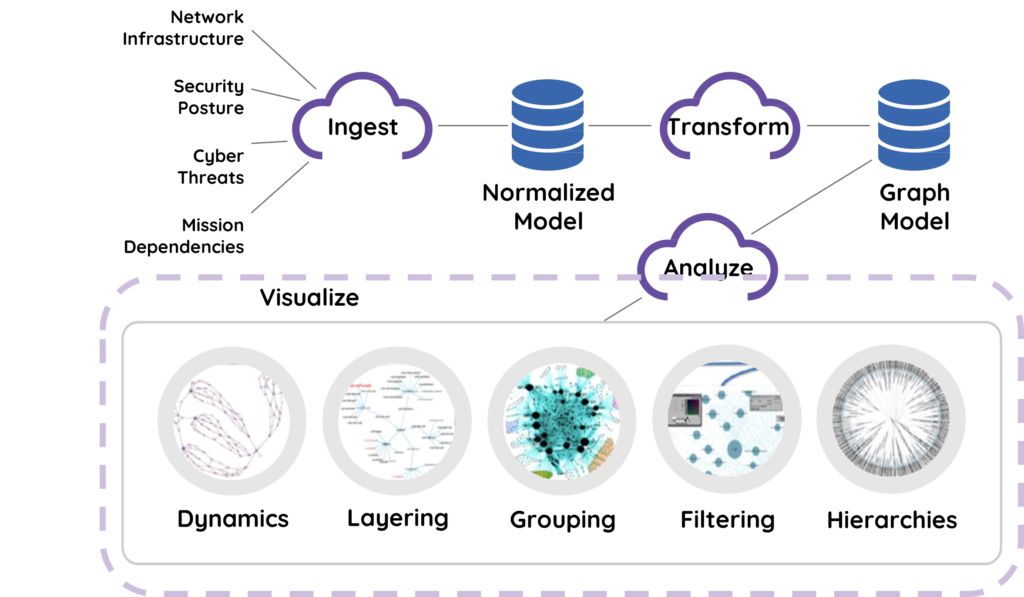
4) Intelligent and Contextual Visualizations to highlight priorities and secure your Enterprise
- See vulnerabilities and gain context to react appropriately to attacks and protect mission-critical assets
- Analyze It, See It, and Turn it into ACTION
- Continuously assess security posture in real-time against cyber threats!






