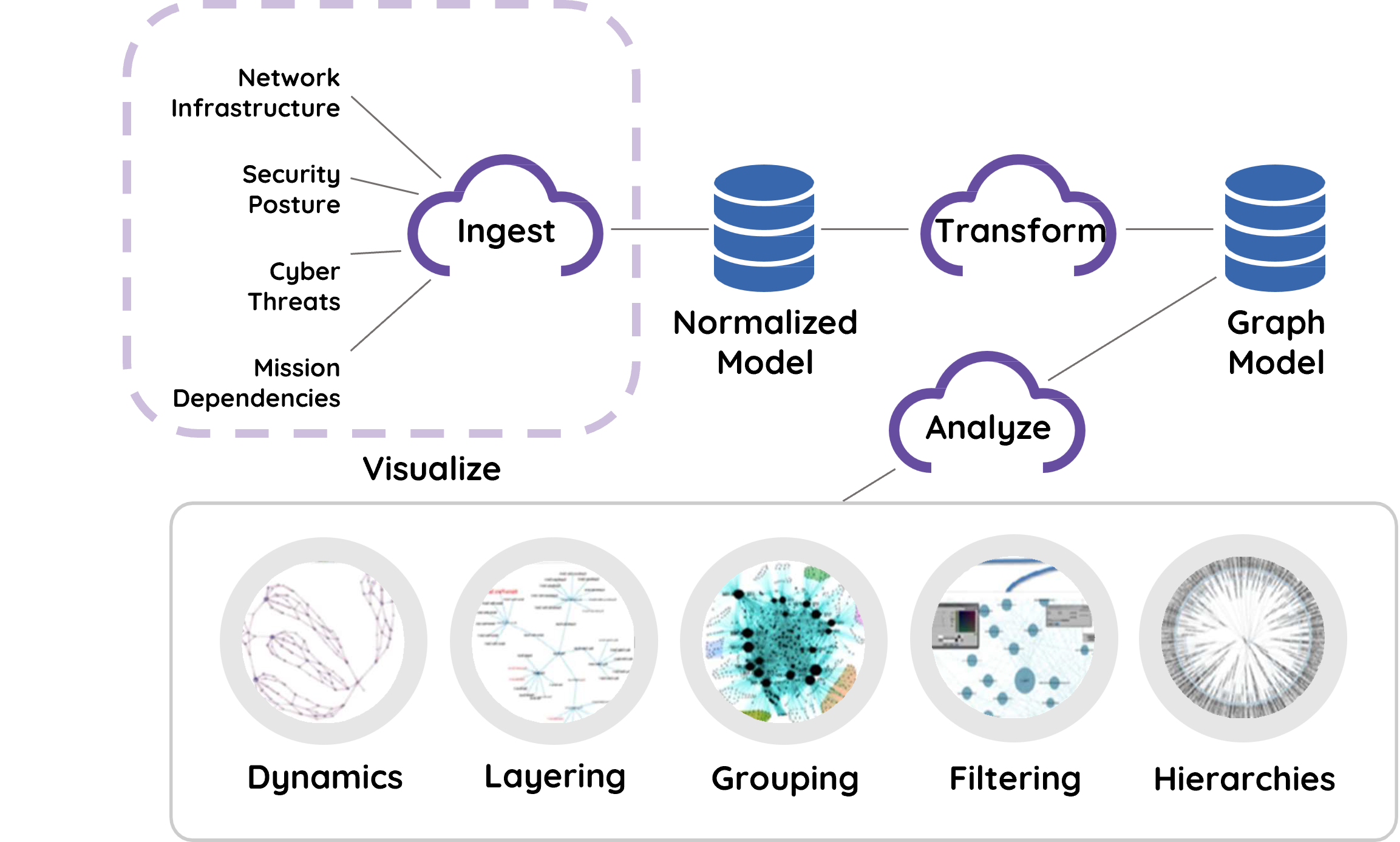
FAQ – Frequently Asked Questions
To Visium Technologies shareholders and interested investors: We often receive questions from interested parties at info@visiumtechnologies.com, and therefore are providing this first in a series of answers to Frequently Asked…